Check out Our Products
Professional Penetration Testing Services
Protect your infrastructure with expert security assessments. We identify vulnerabilities before attackers do.
Comprehensive Testing
Web, Cloud, Network & MoreCertified Experts
Why Choose Guardyk?
- Proactive Security: Find vulnerabilities before attackers exploit them
- Industry Experience: Startups to Fortune 500 companies
- Detailed Reporting: Actionable insights with clear remediation steps
- Compliance Ready: PCI DSS, HIPAA, GDPR & More
$4.44 Million
Latest Tutorials
Fresh content to keep you ahead in AI and cybersecurity. Learn from the latest techniques and methodologies.

Preparing for Your Next Web Pentest
A practical guide to pre-attack reconnaissance: setting engagement rules, Google dorking, discovering subdomains and endpoints, identifying tech stacks and WAFs, and mining JS files for secrets using tools like Subfinder, Wayback Machine, and Wappalyzer.

Step-by-Step Metasploitable2 Exploitation Guide for Penetration Testing and Vulnerability Assessment
A complete, beginner-friendly penetration testing tutorial for cybersecurity students, SOC analysts, and aspiring penetration testers.

How to Crack Locked PDFs
Learn how to crack password‑protected PDFs using pdfcrack. This concise guide covers PDF encryption basics, how pdfcrack approaches password cracking and choosing wordlists.
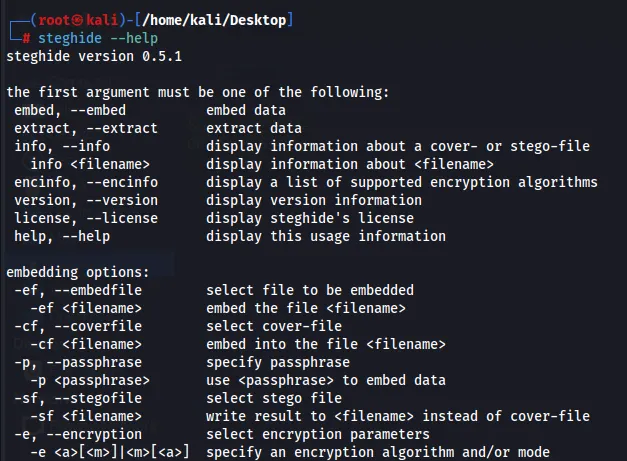
How to Perform Steganography Using Steghide
Learn to hide and retrieve data inside images and other files using steghide. This concise guide covers embedding/extraction, passphrase use, and safe, legal applications.
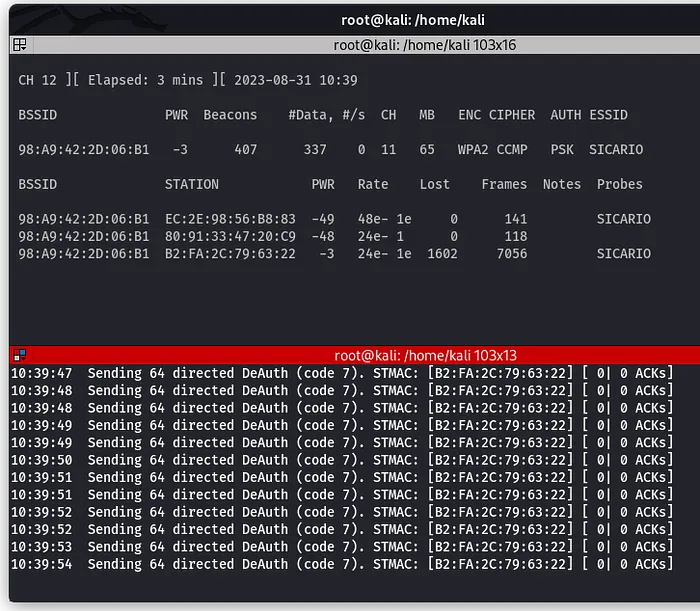
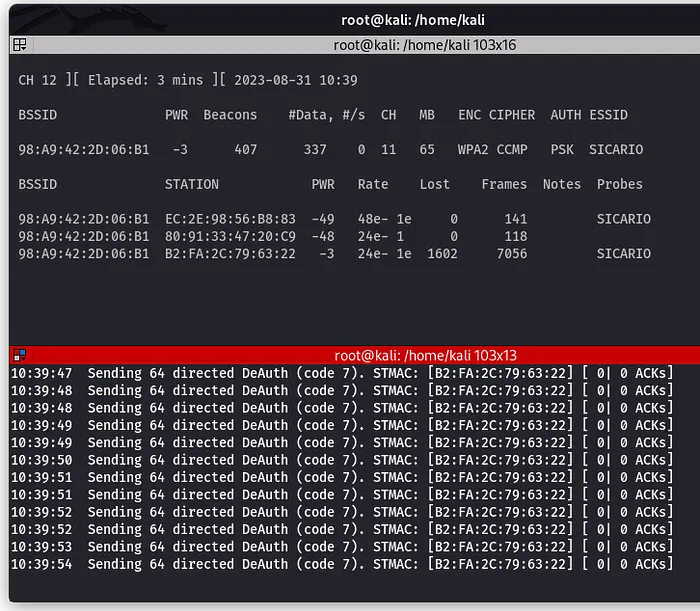
How to Perform a Wi-Fi Deauthentication Attack
Learn how Wi-Fi deauthentication attacks work and how targets can be forcibly disconnected from a network. This tutorial explains the concept and demonstrates the process in a controlled environment.

How to Recover Deleted Files Using Foremost
Learn how to recover deleted files using Foremost, a powerful forensic tool for file carving. This guide walks you through scanning storage devices for lost data and restoring deleted images, documents, and archives with ease.
Explore Categories
Browse tutorials by topics.
Check Out Our Security Tools
Free cybersecurity tools to enhance your digital security. Protect yourself with our privacy-focused security utilities.
Password Breach Checker
Check if your password has been exposed in data breaches using secure K-anonymity technology.
Password Strength & Generator
Analyze password strength and generate cryptographically secure passwords with customizable options.
Encryption/Decryption Tool
Securely encrypt and decrypt text using industry-standard algorithms. Supports both symmetric and asymmetric encryption.
Privacy-First Security Tools
All our tools are designed with your privacy in mind. No data storage, client-side processing, and transparent security practices.
Explore All Tools