Check out Our Products
Professional Penetration Testing Services
Protect your infrastructure with expert security assessments. We identify vulnerabilities before attackers do.
Comprehensive Testing
Web, Cloud, Network & MoreCertified Experts
Why Choose Guardyk?
- Proactive Security: Find vulnerabilities before attackers exploit them
- Industry Experience: Startups to Fortune 500 companies
- Detailed Reporting: Actionable insights with clear remediation steps
- Compliance Ready: PCI DSS, HIPAA, GDPR & More
$4.44 Million
Latest Tutorials
Fresh content to keep you ahead in AI and cybersecurity. Learn from the latest techniques and methodologies.

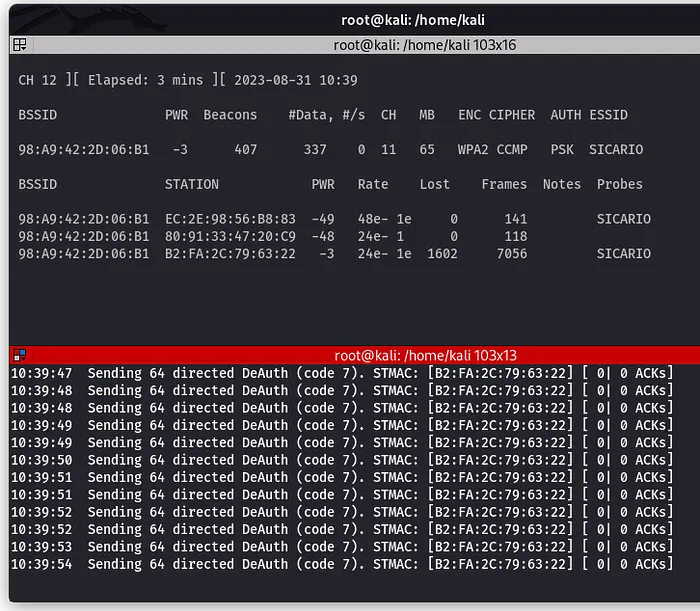
How to Install Kali Linux on VirtualBox
Learn how to install Kali Linux on VirtualBox step by step, even if it's your first time setting up a virtual machine. This guide covers both installing Kali using the ISO file and using the pre-built VM, so you can quickly create a safe environment for practicing cybersecurity and penetration testing.
What Are Hosts in Cybersecurity?
This tutorial explains what hosts are in cybersecurity, why every network-connected device is a potential attack surface, and how attackers target them. It also covers defensive strategies like host hardening, EDR, patch management, and asset discovery to protect organizational networks.

The Dark Web: A Beginner's Guide to Accessing & Navigating It
The dark web sounds scarier than it is. In this guide, I show you how to access it using Tor, and take you on a tour of some of the wildest sites hiding beneath the surface of the internet.

Dark Web vs Deep Web: What's the Actual Difference?
Confused about the dark web and deep web? You're not alone. Most people use these terms interchangeably, but they're completely different things. This guide breaks down the actual differences, size comparisons, and what you'll really find in each part of the hidden internet.

Searching for a Trafficked Person Using Open Source Intelligence (OSINT)
Learn how Open Source Intelligence (OSINT) can be used to locate missing or trafficked persons by analyzing publicly available data such as phone numbers, online ads, images, and social media traces. It explains real-world techniques, tools, and investigation strategies that turn scattered digital footprints into actionable leads.

How to Create and Use Wordlists for Password Testing
Learn to create and use wordlists for authorized password testing. This guide covers built-in wordlists like rockyou.txt, generating custom wordlists with Crunch, and understanding why password predictability matters for security.

Preparing for Your Next Web Pentest
A practical guide to pre-attack reconnaissance: setting engagement rules, Google dorking, discovering subdomains and endpoints, identifying tech stacks and WAFs, and mining JS files for secrets using tools like Subfinder, Wayback Machine, and Wappalyzer.

Step-by-Step Metasploitable2 Exploitation Guide for Penetration Testing and Vulnerability Assessment
A complete, beginner-friendly penetration testing tutorial for cybersecurity students, SOC analysts, and aspiring penetration testers.

How to Crack Locked PDFs
Learn how to crack password‑protected PDFs using pdfcrack. This concise guide covers PDF encryption basics, how pdfcrack approaches password cracking and choosing wordlists.
Explore Categories
Browse tutorials by topics.
Check Out Our Security Tools
Free cybersecurity tools to enhance your digital security. Protect yourself with our privacy-focused security utilities.
Password Breach Checker
Check if your password has been exposed in data breaches using secure K-anonymity technology.
Password Strength & Generator
Analyze password strength and generate cryptographically secure passwords with customizable options.
Encryption/Decryption Tool
Securely encrypt and decrypt text using industry-standard algorithms. Supports both symmetric and asymmetric encryption.
Privacy-First Security Tools
All our tools are designed with your privacy in mind. No data storage, client-side processing, and transparent security practices.
Explore All Tools